Concerns persist over cloud security

Cloud security is called into question by a series of recklessness and bad practices as denounced in a study by Varonis.
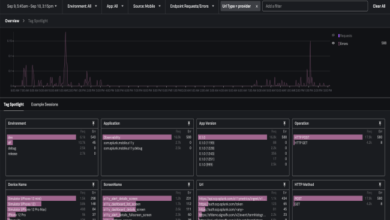
The very principle of the cloud is to delegate the management of an infrastructure or more to specialists. But that doesn’t mean that the corporate client shouldn’t do anything. Varonis has just published a study which highlights the very frequent presence of bad practices in the management of identities and rights, bad practices jeopardizing the security of cloud instances which are technically secure.
Thus, within the scope of the study, 43% of identities with rights to instances are obsolete, unused and abandoned. However, these identities have retained their rights and are more likely to be discreetly hijacked, generating an attack surface that is as considerable as it is avoidable. It is essential to regularly “clean up”. Worse: three out of four identities corresponding to external service providers who have ceased their work are still active. “Non-human” identities (corresponding to various robots such as APIs, applications, etc.) are also multiplied here: one in four identities for SaaS, one in two for IaaS. Are they all necessary?
Even on the identities to keep, some care must be taken. Thus, the rights granted are too broad in relation to the needs in 44% of cases, 60% of the administrators thus not having to be, for example. 16% of identified accounts perform administrative tasks to which they should not have access, 20% have access to sensitive data and 15% transfer data from a corporate cloud to a private account where, by definition, it there can no longer be any control.