Hacking Cloud Resources Has Never Been Easier According to IBM X-Force
IBM publishes its annual report, X-Force, on existing cyber threats in 2021. Largely in the cloud, these threats have increased by 150% since 2016.
As cybercriminals use their imaginations to take on businesses, IBM Security X-Force’s latest report sheds light on their key tactics, ranging from open doors users leave behind, to the burgeoning market for stolen cloud resources on the dark web. Proper configuration of applications, databases and policies could prevent many breaches of cloud environments, observes IBM. The X-Force report on the cloud security threat landscape covers the second quarter of 2020 until the second quarter of 2021. We learn that two out of three cloud-related incidents are due to a misconfiguration of the interface. application programming (API). The same goes for virtual machines, poorly configured and whose default security settings were mistakenly exposed on the internet, with more than insufficient network controls.
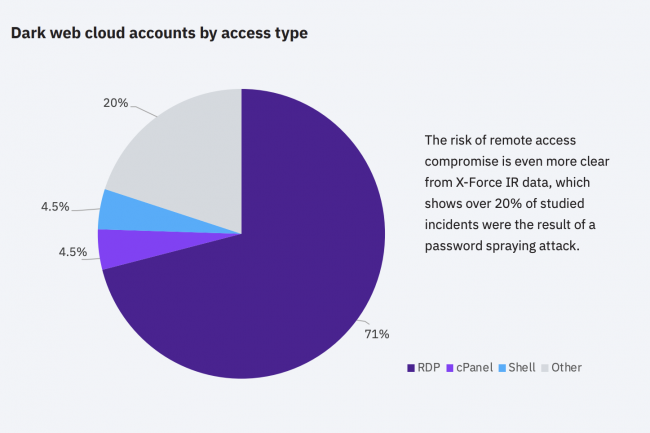
The X-Force Red team also observed password breaches during penetration tests on cloud services carried out during the year 2021. The team also observed a significant increase in the severity of vulnerabilities in applications. deployed in the cloud. The number of flaws detected in these applications has thus jumped by 150% – 2,500 have been recorded – since 2016. According to the report, nearly 30,000 compromised cloud accounts are for sale – at low prices – on the dark web, says IBM. . The RDP protocol also represents 70% of cloud resources for sale.
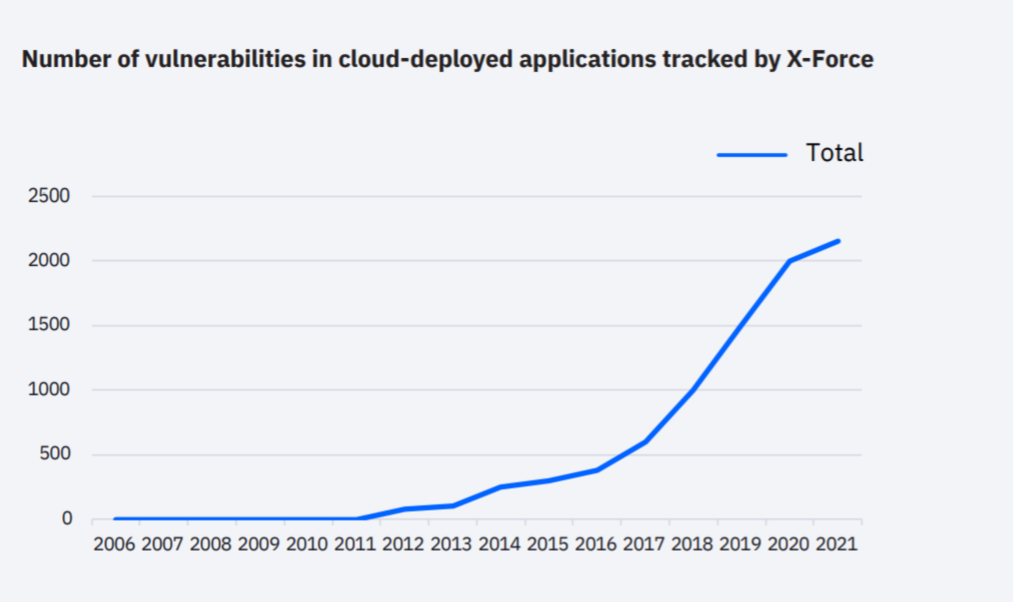
Ransomware continues to gain illicit access to cloud data, and the number of attacks is growing rapidly. (Credit: IBM)
Hybrid cloud to mitigate attacks
The 2021 Cost of a Data Breach report found that organizations affected by incidents implementing a predominantly public or private cloud-centric approach experienced breach costs that were approximately $ 1 million higher than those from organizations that have adopted a hybrid cloud approach. Adopting a heterogeneous environment helps to better control data storage. Faced with this, the modernization of critical applications remains the only possible solution. Not only will security teams be able to recover data faster, but they will also have a much more holistic view of the threats facing their organization, so that they can react more quickly.