Comcast takes over SD-WAN specialist Masergy
The acquisition of Masergy, a company specializing in software-defined networks, will give Comcast Business a boost in the SD-WAN and SASE networks for enterprises.
Comcast intends to revive its corporate network business. The American operator has just announced its intention to acquire the company Masergy Communications, a specialist in SD-WAN and cloud-based security. While Comcast is a listed company, Masergy is not, so the terms of the deal were not disclosed. Remember that Masergy was bought by the investment fund Berkshire Partners in 2016.
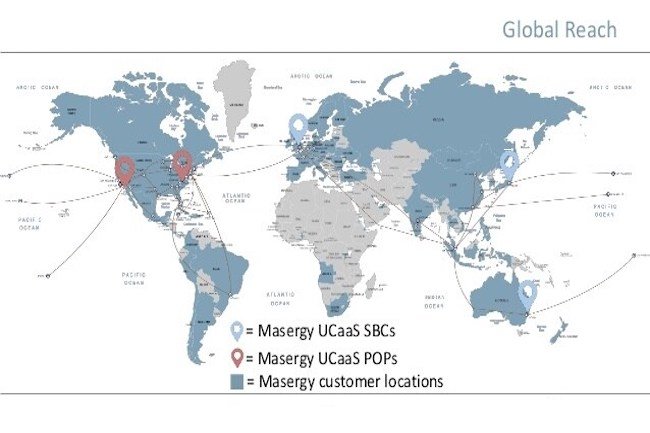
Comcast currently has its own SD-WAN offering through a partnership with Versa Networks, but it is aimed at small businesses. The acquisition of Masergy gives the operator better access to businesses. Masergy specializes in managed SD-WAN and secure communications, as well as cloud-based unified communications solutions. The company claims to have more than 1,400 customers in nearly 100 countries.
Services with key partners
Masergy’s offering includes managed SD-WAN solutions, unified communications as a service (UCaaS), call centers as a service (CCaaS) and managed security solutions. Its SD-WAN and SASE (secure access service edge) services are provided by Fortinet, while its CASB (cloud access security broker) is provided by Bitglass and its UCaaS is offered in partnership with Cisco Webex. But most importantly for Comcast is that Masergy has a mature distribution program that it has built over its 20 years in business. The acquisition of Masergy represents a significant leap forward for Comcast’s business ambitions. This gives Comcast a boost in its desire to compete with Verizon and AT&T, plus it helps diversify its business at a time when consumers are moving away from cable television.